/!\ Disclaimer /!\
Everything presented in this blog is for educational and research purposes only. I am not responsible for any damage or issues that may arise from following these steps. Use this information at your own risk.
Introduction
In this blog post, I'll explain a technique for extracting IPAs and testing iOS applications without requiring a jailbroken device. I discovered this approach after watching certain Apple WWDC22 videos. While writing this post, I found two other community articles discussing similar methods but with different approaches. You'll find links to these resources in the References section.
I think everyone reading this post can agree on one thing:
MOBILE APPLICATION TESTING IS PAINFUL, ESPECIALLY TESTING iOS APPLICATIONS
Over the past few weeks, I've been researching various options, techniques, and tools for iOS application pentesting. In all the posts I've found, many crucial details are missing. As we know in this field, nothing is purely Black or White - we're always working in Gray. I want to clarify a few important points:
- If possible, ALWAYS ask the client to provide an unencrypted IPA. This will save you countless headaches and allow you to test on a non-jailbroken device.
- NOT all IPAs can be decrypted statically. For example, when testing an application that only runs on newer iOS versions, you might not be able to decrypt the IPA on an older jailbroken device. In such cases, you'll need more complex reverse engineering techniques that won't be covered in this blog.
- In this blog, we'll learn how to download IPAs from the official App Store using non-jailbroken devices. In future posts, I'll cover how to statically decrypt these applications (when possible), patch them, and install them on non-jailbroken devices for pentesting.
- I'll explain the methodology and tools I used to discover this technique and obtain IPAs from the App Store.
Essential Background Context
The first thing every beginner in iOS application testing needs to understand is that YOU CANNOT JAILBREAK ANY iOS VERSION YOU WANT. I won't go into detail about what a jailbroken device is or which versions are affected, as there's no better resource than:
One of the most common situations you'll encounter when testing an iOS application on an older device is:

Click to expand
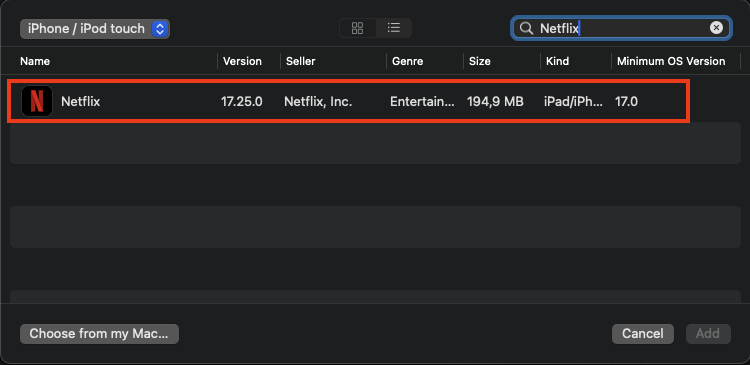
Not Supported iOS Version
As you can see in the image below, this iPhone runs iOS 16.7.10, which is almost the latest version that iPhone X supports (16.7.11), making it impossible to install the app directly from the App Store and make it work.
Click to expand
iphone
With some understanding of Apple's architecture and philosophy, and inspiration from the WWDC22 video Bring your iOS app to the Mac, I started investigating whether there was a way to "trick" a legitimate Apple app into downloading the IPA on macOS.
Summary
For those who are impatient and want to try the research on their own or those who don't have time to read the entire blog, here's a summary of the steps I took to download IPAs from the App Store without a jailbroken device:
-
Using AI for initial research
- Started with a Google search using its new integrated AI
- The AI generated a list of potentially relevant tools
- Expanded and refined the search with Perplexity, obtaining more detailed results
-
Identifying Apple Configurator as a key tool
- After filtering results obtained with Perplexity, found Apple Configurator as a relevant option
- Notable because it allows installing and managing applications on Apple devices
-
Analyzing processes with Red Canary Mac Monitor (Procmon for macOS)
- To investigate Apple Configurator's behavior, used Red Canary Mac Monitor
- This software monitors macOS processes similar to Procmon on Windows
-
Monitoring application installation
- During installation through Apple Configurator, recorded system activity
- Applied filters in Mac Monitor to focus on .IPA files (iOS/macOS app formats)
- Successfully identified relevant system activity related to the installation
With the above steps, we can download IPAs from the App Store, but we still have some challenges to overcome before we can test the application on a non-jailbroken device:
- Modify the IPA to install it on an unsupported device (Defeating Apple's FairPlay DRM)
- Decrypt the IPA
- In this blog, we'll see how to statically decrypt the IPA (I'm still studying other ways to reverse engineer this type of application)
- Inject the Frida gadget to conduct pentesting directly with Frida or Objection
Obtaining the IPA
Apple Configurator
Apple Configurator is a macOS application that allows you to configure and deploy multiple iOS, iPadOS, and tvOS devices in educational and enterprise environments.
- Download it here: Apple Configurator
Once you've downloaded the application, simply click Add + -> Apps in the top menu and log in with your Apple ID.
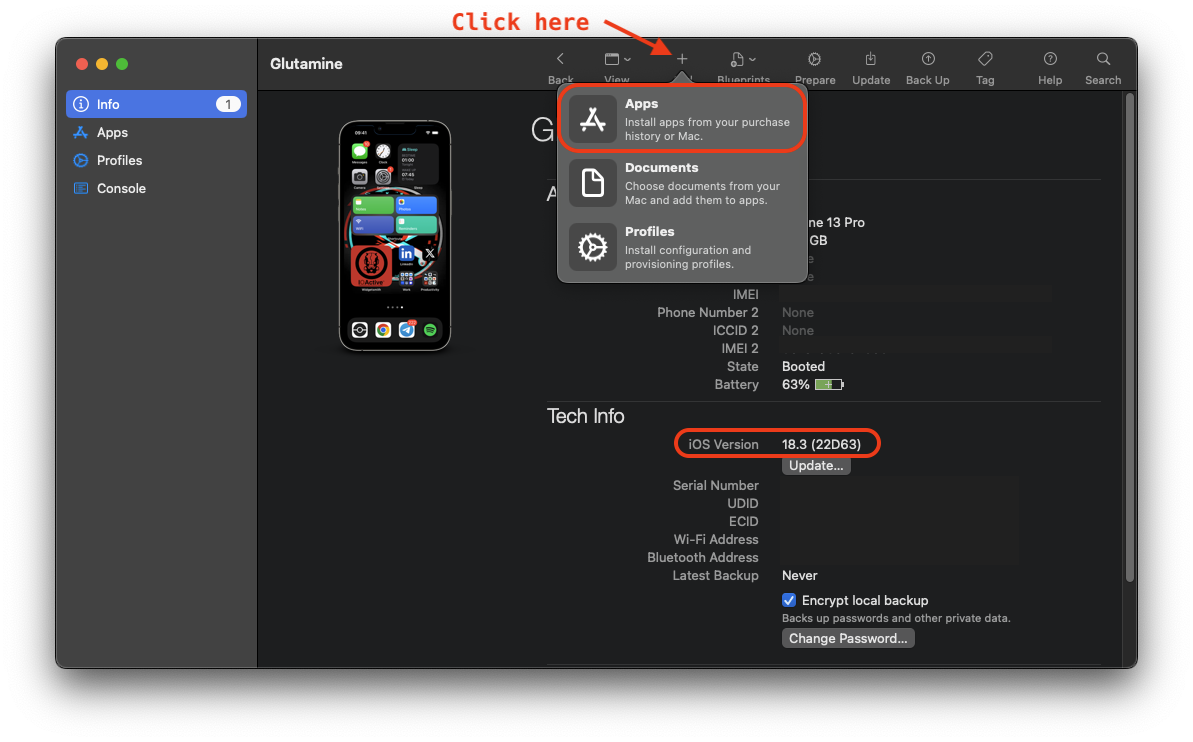

Click to expand
configurator
After logging in, you can download any App Store application that you've previously downloaded using that Apple ID. Click Add.
I recommend having the application pre-installed on your phone to avoid repeating this step twice.Click to expandnetflix
In parallel, you should have Red Canary Mac Monitor and/or Console (a native macOS application) open to monitor all system calls being made. Filter for IPAs to see if any calls are placing the IPA somewhere in the system.
Red Canary Monitor
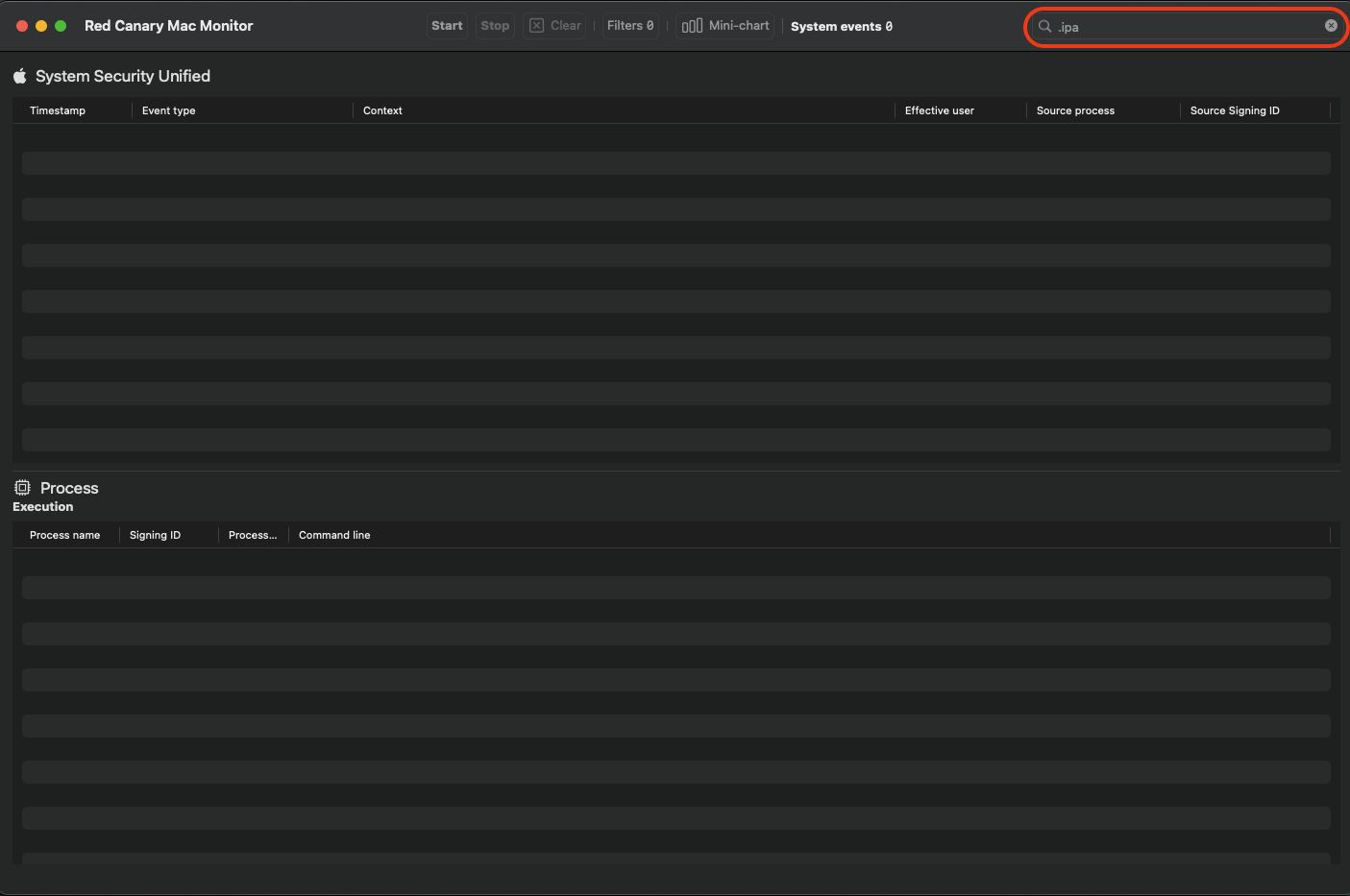

Click to expand
redcanary
Console
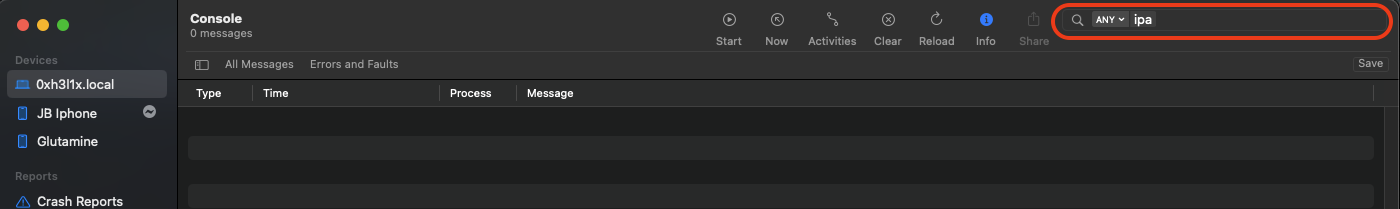

Click to expand
console
Once you click Add (and if you already have the application installed), you'll see the following error:
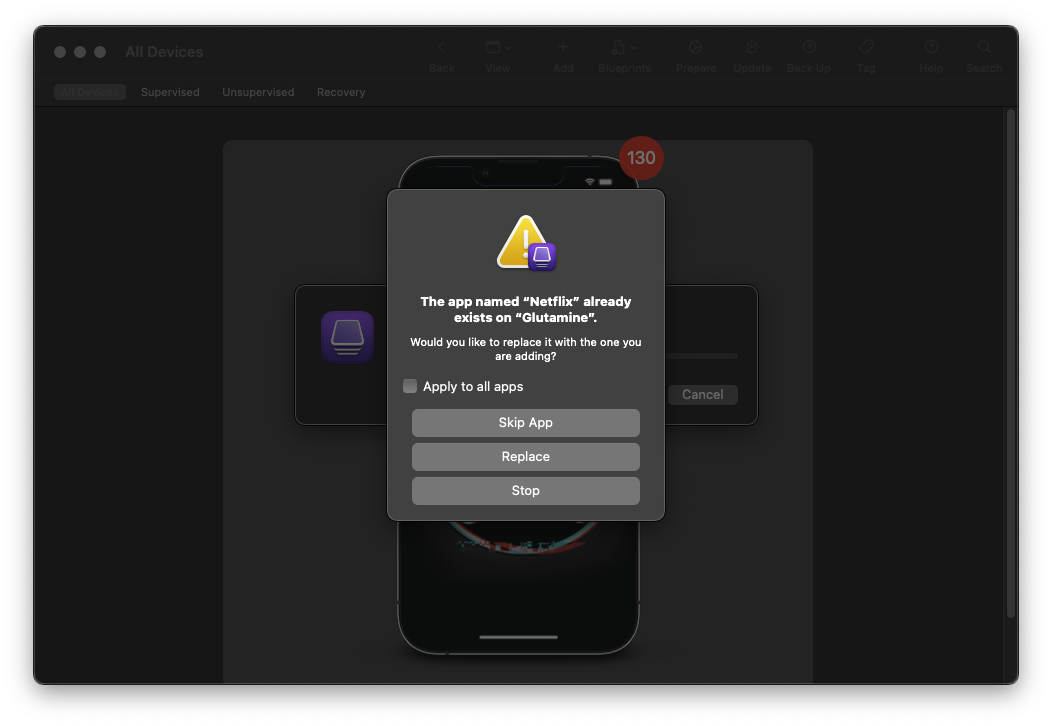

Click to expand
error
Some applications that you download will be placed in Quarantine by macOS, and you won't be able to access them directly until you release them from quarantine (as is the case with the Netflix application).
During the process, you'll see in your monitoring application that the IPA is being temporarily downloaded to the directory /Users/[username]/Library/Group\ Containers/K36BKF7T3D.group.com.apple.configurator/Library/Caches/Assets/TemporaryItems/MobileApps.
Red Canary Monitor
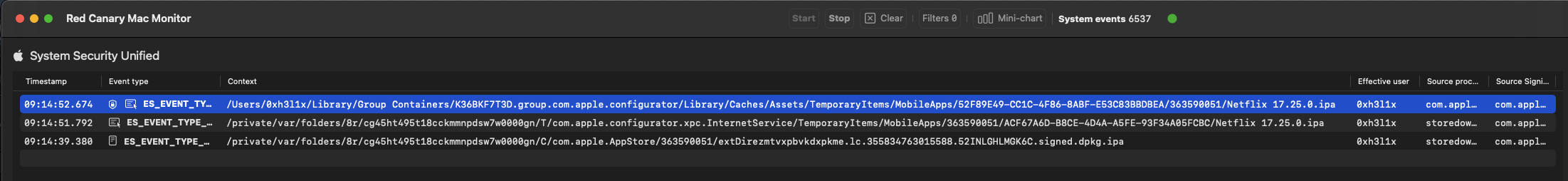

Click to expand
redcanary
Console
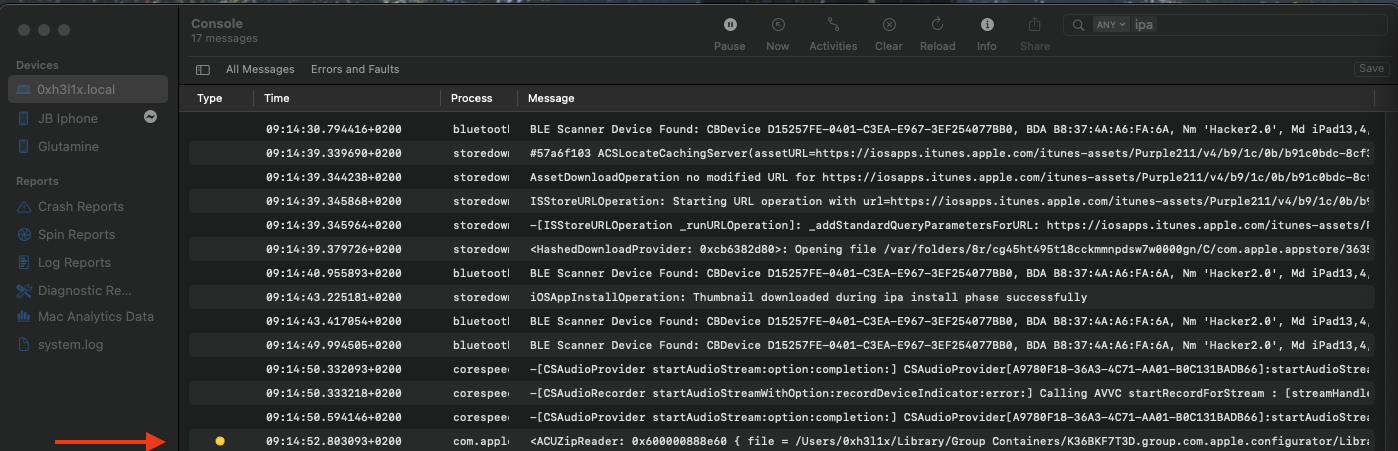

Click to expand
console
As mentioned earlier, certain IPAs are quarantined by Apple, and you can't access them directly, as you can see in the following screenshot:
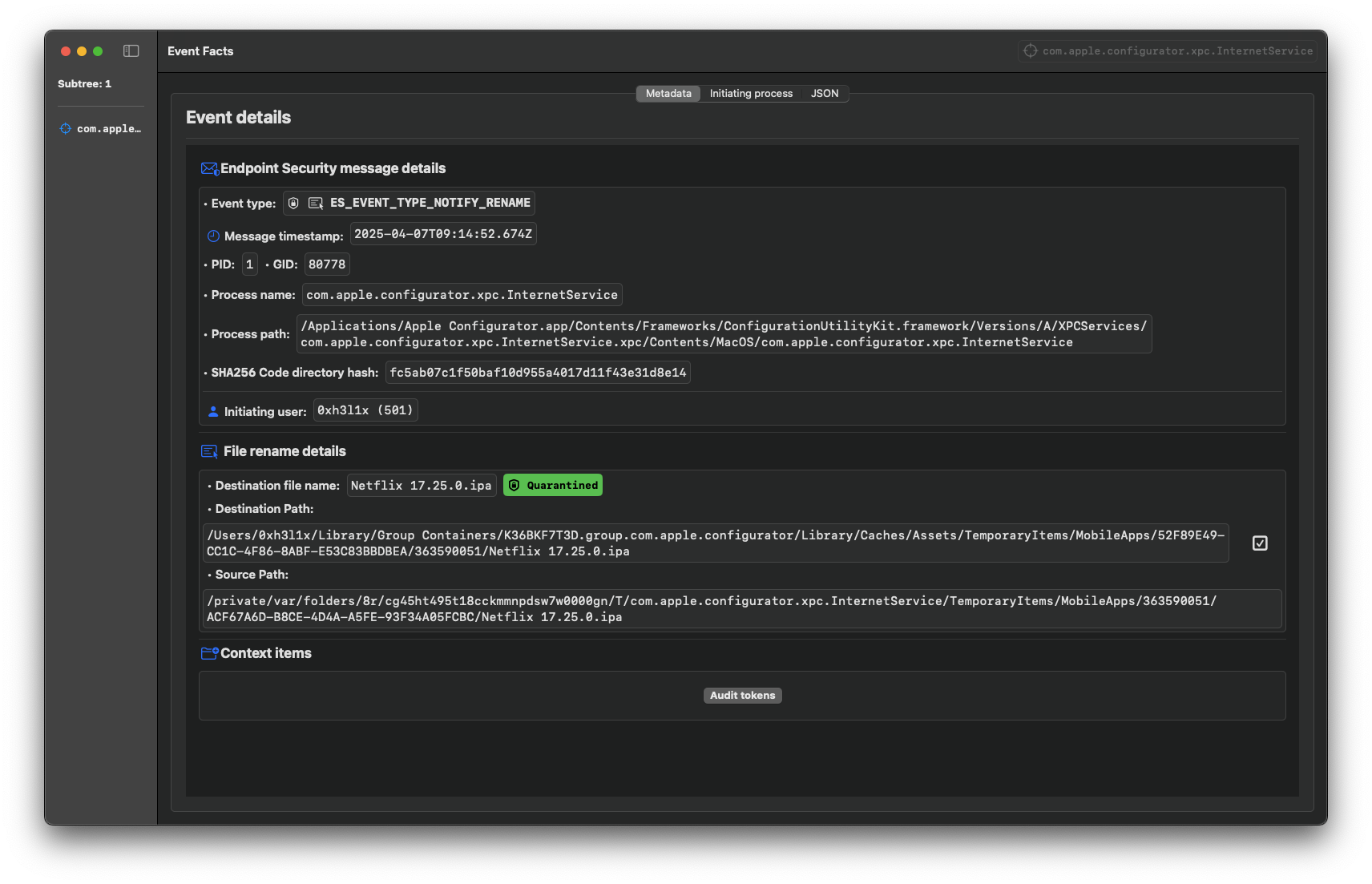

Click to expand
quarentine
In this case, we just need to run xattr on the IPA directory, and we'll be able to access it without any issues:
BASH$ xattr -d com.apple.quarantine /Users/[username]/Library/Group\ Containers/K36BKF7T3D.group.com.apple.configurator/Library/Caches/Assets/TemporaryItems/MobileApps/[IPA]
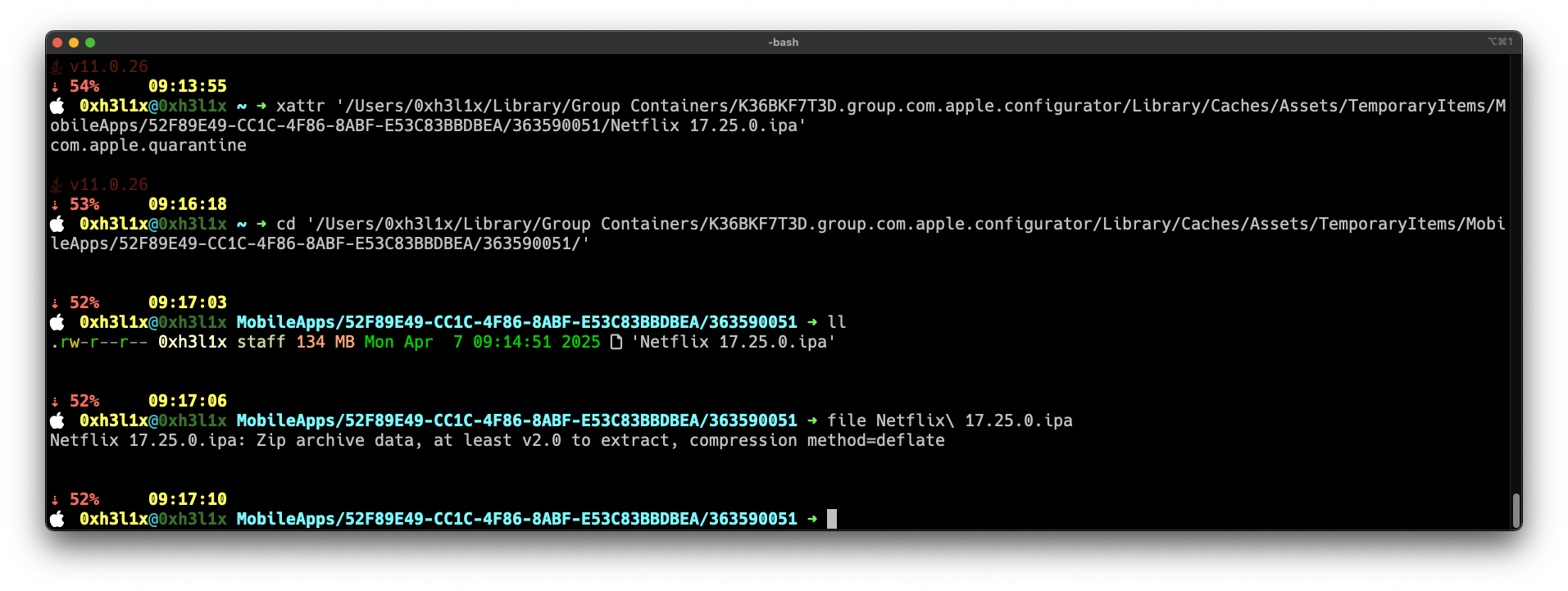
Click to expand
checkterm
Static IPA Decryption
This is one of the most controversial sections in nearly all the posts I've read on this topic because NOT ALL applications CAN BE DECRYPTED STATICALLY, which is rarely mentioned!
IPA files are essentially ZIP files on steroids. Now that we have the IPA in our system, we'll unzip it and modify Info.plist (located under app-unzipped/Payload/[redacted].app). This file contains the MinimumOSVersion attribute (in this case, I changed it to 14.0), which we'll modify to an earlier iOS version, allowing us to install the IPA on a device with an iOS version lower than what the application officially supports.
BASH$ unzip <redacted>.ipa -d app-unzipped $ cd app-unzipped $ open app-unzipped/Payload/<redacted>.app/Info.plist $ zip -r ../custom-version.ipa * (important to do it this way because otherwise, the IPA won't be installable since it won't find the Payload directory) $ cd ..
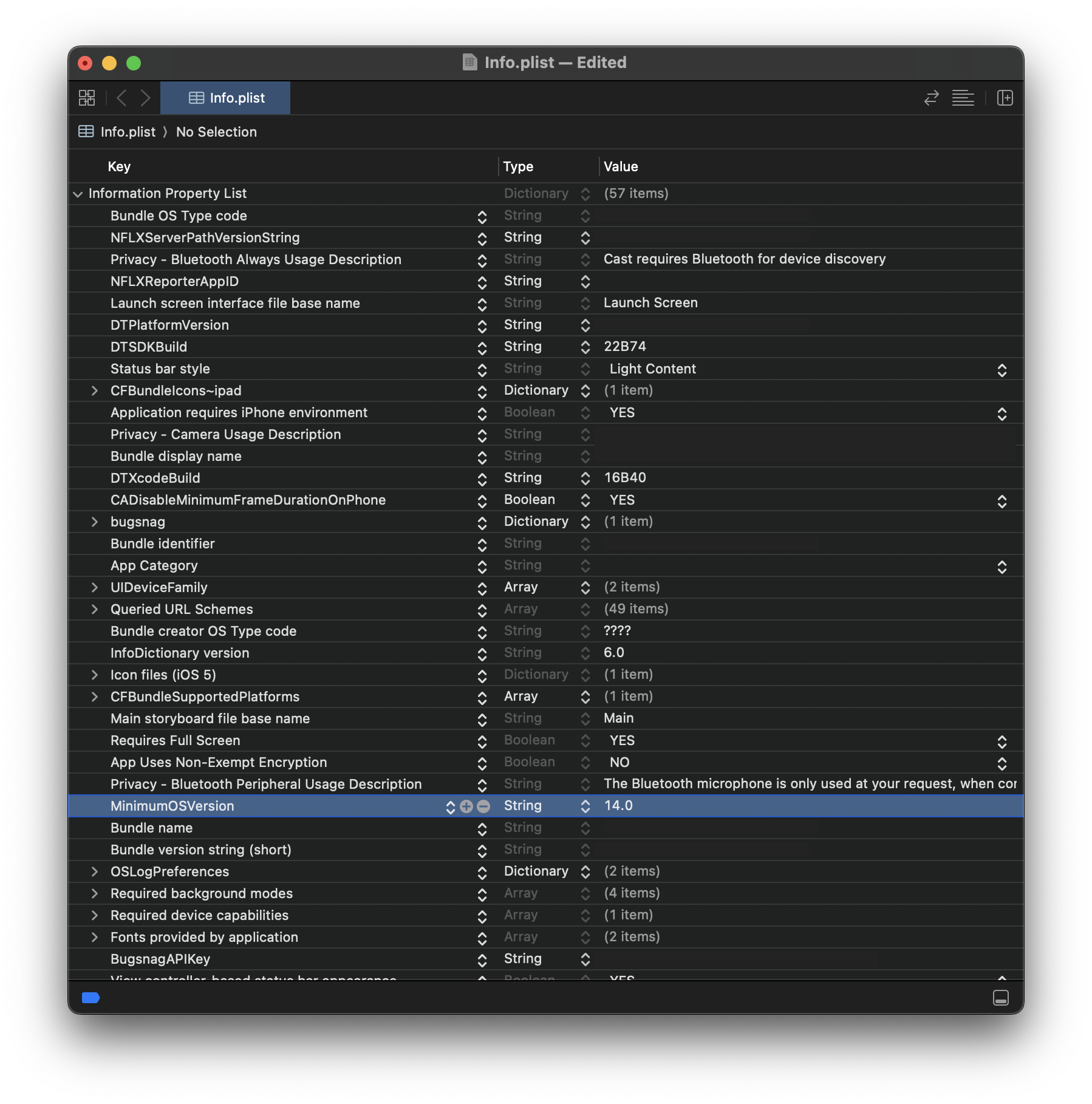
Click to expand
censored
To load the IPA onto the iOS device, I typically use one of these tools:
BASH$ ideviceinstaller -i custom-version.ipa $ ios-deploy --bundle app-unzipped/Payload/<app>.app -W -d $ sideloadly (if you want a graphical interface)
Conclusion
We've seen how to download IPAs from the App Store without needing a jailbroken device and how to modify them to install on a device with an iOS version lower than officially supported. In the next post, we'll cover how to decrypt the IPA and patch it to inject the Frida gadget, enabling pentesting on a non-jailbroken device.